Complete the form below and one of our team members will contact you with all the information required to book your Team Building Day.
Terrorism and the future of our security
I am currently completing a master’s degree in the fields of Terrorism, Safety and Security so I can further increase my knowledge and expertise in these areas.
Today we have access to the latest and most advanced technology, which assists our everyday living such as electronic technology including bank ATM’s, the internet for online shopping or to pay accounts, search engines that have replaced books that satisfy our curiosity. Technology has also advanced our communication capabilities providing devices such as small smart portable telephones and tracking systems, including portable GPS tracking devices for driving through our cities and regional areas, not to mention social media such as Twitter and Facebook.
However, the advanced technologies we take for granted and marvel at, can also work against us, which I will explain to you later in this article. Just think how these advanced technologies could be used whilst possessed by terrorists or transnational criminals. I would suggest that our future could be quite bleak.
Twenty years ago technology was so very different and not as advanced. In those days the height of technology was a very large and cumbersome mobile telephone, with a very restricted range and personal pagers. Many criminals, drug dealers and gang members possessed mobile telephones usually long before many police organisations sought to purchase and distribute them to their front line staff. Computers were the size of small buildings and a personal computer was a Commodore 64 computer, there was no such thing as a ‘laptop’. Law enforcement agencies used CB radios or communications systems that anyone could listen in, to what was being communicated, including the criminals.
Twenty years later criminals are still using mobile telephones but they are also utilising the readily available advanced technology to build their own private communications networks, as pictured below, which has been deployed in all 31 states of Mexico by the Zeta drug cartel. This is a drug cartel that had a national encrypted radio communications system built for their criminal operations and one that prevented any law enforcement interceptions.
Think about that for a moment; think about the innovation that went into that network, the cost of the investment to purchase the various infrastructures and to actually build the network.

Above: The Zeta drug cartel’s encrypted mobile phone network
We consistently underestimate what criminals and terrorists can do. Technology has made a world increasingly open and accessible, which, for the most part is convenient and advantageous for us all but all this accessibility may have unintended or possibly dire consequences.
Consider the 2008 terrorist attack in Mumbai, India and the nature of that attack. The terrorists that carried out that attack were armed with fully automatic weapons such as the AK-47 assault rifles (Avtomat Kalashnikova – model 1947) explosives and hand grenades. The hand grenades were used on innocent people that were sitting in cafes or who were waiting for trains to convey them home after finishing work.
The use of explosives and weapons in terrorist operations is not a new concept. What was a new concept, in this attack, was the terrorists’ use of modern technology and communications to locate and identify additional victims and to provide detailed knowledge and information of the vicinity. The terrorists were armed with mobile phones with internet access providing access to satellite imagery. They possessed satellite phones and some even used night vision goggles but perhaps their greatest innovation was a command/control centre. We have all seen pictures like the one below on television, movies and in the news.

This is an operations centre and the Mumbai terrorist group built their very own operations centre across the border in Pakistan. The terrorists used this operations centre to monitor various media outlets such as the BBC, Al Jazeera, CNN and the Indian local stations. The centre also monitored the internet and social media in order to gauge the progress of their attacks, ascertain how effective their attacks were and how many people they had killed. They did all of this in real time.
At one point during the 60 hour siege the terrorists were going room to room in their attempts to locate additional victims. They went into a suite on the top level of the hotel, kicking down the door and found a man hiding by his bed.
When questioned by the terrorist, this man replied, “I’m just an innocent school teacher.”
Of course the terrorists were well aware that no Indian school teacher could afford to stay in a suite at the Taj Mahal Palace in Mumbai. The terrorists located this male person’s identification and with the use of a mobile telephone they communicated this person’s name to their command centre, where his name was searched using a popular search engine on the Internet. From the search the terrorists located a photograph of this person and called their operative on the ground to clarify their hostage’s features.
As a result the terrorists were able to identify that the male hostage was not a school teacher but the second wealthiest man in India and after discovering this information the terrorist at the command centre gave the order to the terrorist on the ground on Mumbai to terminate this man’s life.
We are all concerned about our privacy settings on social media related web pages such as Facebook, but the fact of the matter is that our openness and the easily accessible information obtained from the Internet, can be used against us. The above example from the Mumbai siege clearly demonstrates that terrorists are now using all available information to make their terror operations easier to conduct. A search engine on the internet can now determine who shall live and who shall die. This is the world that we live in today.
During the Mumbai siege the terrorists were so dependent on technology, that several witnesses were reporting that as the terrorists were shooting hostages with one hand, they were checking their mobile phone messages with their other hand. At the end of the siege three hundred people were seriously wounded, and over 172 people have lost their lives that day, including men, women and children as the terrorists were indiscriminate as to who they killed.
Think about what happened during the sixty-hour siege in Mumbai, ten men not just armed with weapons but also with current technology, were able to bring a city of twenty million people to stand still and this was headline news all over the world. This is what radicals can do with openness and accessibility of technology. This terrorist act occurred nearly four years ago, so what can terrorist do now with the technology available today? An even more worrying question to ponder is what will they do in the future?
The ability of one to affect many is scaling exponentially and it’s not always scaling towards the well intention purposes or uses. It’s not just about terrorism there has also been an enormous paradigm shift in crime, you can now commit a crime that can affect numerous citizens without even revealing your identity.
In the days gone by, a criminal used a knife or a gun to rob a stage coach. Later criminals moved to robbing trains where they could rob more than two hundred people on a train at the same time. This displayed great innovation and later the criminals targeted the banks, to steal larger amounts of cash. Then came the Internet, the Internet allowed opportunities for criminals to scale even more, we all remember the Sony-Play Station Hack, over one hundred million people were robbed. Think about that, when in the history of humanity has it ever been possible for one person to rob one hundred million people? Criminals are not only attempting to scam money from us but they are also stealing our identities as well. Many law enforcement agencies admit that identity fraud is an ever growing crime, which they are unable to prevent.
Off course it’s not just about stealing items or our identity, there are number of other avenues that criminals can exploit such as robot technology and three dimensional (3D) printers which can print in many materials ranging from plastic to metals.
3D printers these days offer a lot of opportunity for the good and the bad for example today they can be used to print guns and many important parts of automatic weapons think about that technology in the wrong hands, think about what would happen when a company of rebels can print their own AK-47s, think about what terrorist can do with this technology.

3D Printer
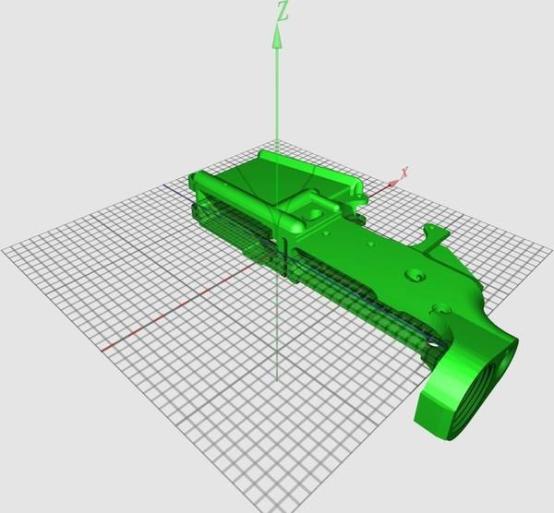
Lower receiver of an AR-15 assault rifle being created
Everyday we’re connecting more and more of our lives to the Internet, which means that the internet containing our identity, lives, memories, thoughts and other things will soon be the internet of things to be hacked. All of the physical objects in our lives and space are been transformed into information technologies and that has a radical implication on our security because more connections to more devices mean more vulnerabilities and criminals, terrorists and hackers understand this. If you control the code, you control the world this is the future that awaits us.
There has not yet been an operating system or technology that hasn’t been hacked, which is disturbing since the human body itself is now becoming part of the technology/information era. Every year thousands of pacemakers, diabetic pumps, and defibrillators are being implanted in people.
In the United States alone there are sixty thousands people who have a pacemaker that connects to the Internet, the defibrillators allows physician at a distance to give a shock to a heart in case the patient needs it. But if you heart does not need a shock and some person or criminal activates the defibrillator the complications could well be devastating, to say the very least.
Of course we are going to go even deeper than the human body, down to the cellular level these days. Up until now all of the technologies I have mentioned have been silicon-based ones and zeros but there is another operating system out there, the original operating system being our Deoxyribonucleic Acid (DNA). To hackers DNA is just another operating system waiting to be hacked.
To criminals and hackers, it is a great challenge for them. There are people already working on hacking the software of life and while most of these scientists and other technicians are doing this for the greater good and to help mankind, some will be doing it to champion more sinister reasons.
So how will criminals abuse this? With synthetic biology you can do some innovative things. For example, I predict that eventually we will move away from a plant based narcotics world to synthetic one. Why do we need plants anymore, when you can just take the DNA code from Marijuana or poppies or coca leaves and cut and paste that gene, place the gene into yeast and cause the yeast to make the cocaine for you, or the Marijuana or any other drug. As to how the criminal element will to use yeast in the future is going to be really interesting, especially as we move towards the next century.
Since 2008 something changed, the technologies became more advanced and now DNA sequencing is proceeding at a pace that is five times greater than that of any legislation to ensure the appropriate controls are in place, which has significant implications for us. It took us 30 years to get from the introduction of the personal computer to the level of cybercrime we have today and even so the legislation has still not been able to catch up with the evolving technology perpetrated during cybercrime. Today, biological breakthroughs and technology is advancing at rapid rates and it is without doubt that the use of bio-terror or crime could well be the way terrorist or criminals operate in the future.
It will be simpler for anyone in the future to go ahead and print their own bio-virus and enhanced versions of anthrax or weaponised flu. In September, an amiable Dutchman stepped up to the podium at a scientific meeting convened on the island of Malta and announced that he had created a form of influenza that could well be the deadliest contagious disease humanity has ever faced. The bombshell announcement, by virologist Ron Fouchier of Erasmus Medical Center, sparked weeks of vigorous debate among the world’s experts on bioterrorism, influenza, virology, and national security over whether the research should have been performed or announced and whether it should ever be published.
Meanwhile, a joint Japanese-American research team led by the University of Wisconsin’s Yoshihiro Kawaoka says that it, too, has manufactured a ‘superflu’. Additionally, a team at the U.S. Centers for Disease Control and Prevention (CDC) in Atlanta has acknowledged doing similar research, without successfully making the über flu. The U.S. National Science Advisory Board for Biosecurity is now deliberating whether to censor publication of the Fouchier and Kawaoka papers, though it lacks any actual power to do so: It could so advise scientific journals, but editors would still decide. The advisory board is expected to release its decision on December 15.
The interest in this brave new world of biology is not limited to the scientific community. U.S. Secretary of State Hillary Clinton made a surprise visit to Geneva on December 7, addressing the Biological Weapons Convention review conference. The highest-ranking U.S. official to speak to the biological weapons group in decades, Clinton warned, “The emerging gene-synthesis industry is making genetic material widely available. This obviously has many benefits for research, but it could also potentially be used to assemble the components of a deadly organism.”
“A crude but effective terrorist weapon can be made by using a small sample of any number of widely available pathogens, inexpensive equipment, and college-level chemistry and biology,” Clinton also stated. “Less than a year ago, al Qaeda in the Arabian Peninsula made a call to arms for and I quote, brothers with degrees in microbiology or chemistry to develop a weapon of mass destruction”.
Noting that, “It is not possible, in our opinion, to create a verification regime for biological weapons compliance under the convention”, Clinton called for voluntary transparency on biological experimentation among the 165 countries that have signed the agreement.
Officials throughout the U.S. government are declining to comment on the influenza experiments or elaborate on Clinton’s comments and appearance in Geneva. The influenza scientists were politely but firmly instructed recently by U.S. officials to keep their mouths shut and provide no data or details regarding their experiments to anybody. Sources inside the Dutch, German, and French governments say that discreet agreement was reached among Western leaders to greet the influenza pronouncements with a wall of silence, pending the advisory board’s decision and detailed analysis of the experiments by classified intelligence and scientific bodies.
You see we can go ahead and create new pandemics and the researchers who did this were so proud of their accomplishments they wanted to publish it openly to gain recognition and provide access to this new information.
But this goes much deeper than that, DNA researcher Andrew Hassell has pointed out quite rightly that if you can use modern cancer treatments to go after one cell, while leaving all the other cells around it intact then you can also go after anyone person’s cells.
Personalised cancer treatments are the flipside of personalised bio-weapons, which means you can attack any one individual including all the world leaders and the people in the picture below.

Some of the questions we should be asking are: How will we protect these people and our children in the future? What can we do about this? I acknowledge that I do not have all the answers but I know some solutions that would give us a good place to start.
The law enforcement system is currently a closed national based system, while the threats are global. Law enforcement doesn’t scale globally in our current system, firearms, border guards, big gates and fences are outdated in our new world into which we are moving.
Strategies and agencies that are currently working well in our world to combat crime, such as the Organized Crime & Corruption Reporting Project (OCCRP), which is a not-for-profit, joint program of a number of regional non-profit investigative centers and for profit independent media stretching from Eastern Europe to Central Asia.

The goal of the OCCRP is to help the people of the region better understand how organised crime and corruption affects their lives. OCCRP seeks to provide in-depth investigative stories as well as the latest news pertaining to organised crime and corruption activities in the region. In addition to the stories, OCCRP is building an online resource center of documents related to organised crime including court records, laws, reports, studies, company records and other public documents that will be an invaluable resource center for journalists and the public alike.
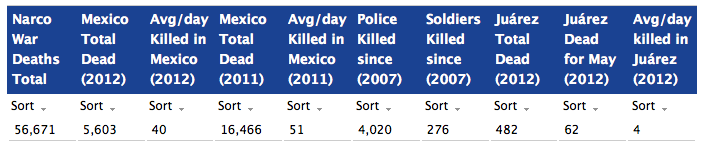
More than 40,000 people have died in drug violence in Mexico since President Felipe Calderon took office in December 2006 and stepped up the fight against organised crime, the Nation’s Intelligence and National Security Director Guillermo Valdes Castellanos said.
In addition Castellanos said, “Mexican authorities and drug gang members have been engaged in 963 gun battles in that time period, or about one per day. The large number of confrontations depict that the government is taking the fight to the drug cartels, which previously operated with impunity.”
We know that technology can be used more potently for good. As more people around the globe become connected, they see, read and hear more. Greater access leads to stronger demands for accountability. We believe the spread of modern devices and access for those most threatened will create a virtual, albeit nascent, counterweight against the world’s worst criminals. Even stubborn governments will one day have to meet their citizens’ rising expectations.
WM Consulting is a website devoted to tracking the number of narcotic related killings in Mexico on Google Maps. The map below represents the killings from May 10, 2010 to June 11, 2010.
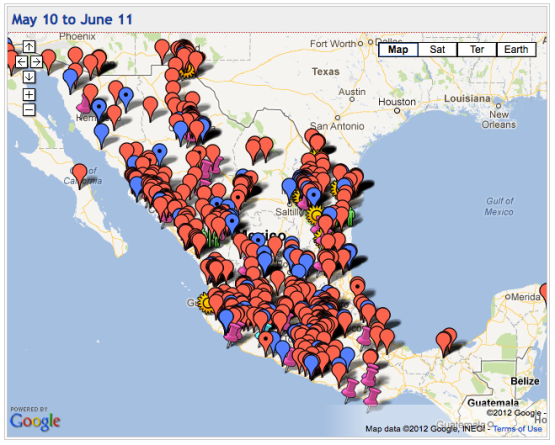
The red balloons represent civilians killed. The red balloons with a dot are high profile killings. Light blue pushpins are journalists and the purple pushpins for politicians. The blue balloons are police officers and soldiers (and other law enforcement). The blue balloons with a dot are high-ranking law enforcement officers. The yellow suns represent car bombs while the two green people represent mass graves.
I firmly believe that we would obtain better results in fighting crime and terrorism together as a united front, rather than doing nothing and relying on governments and law enforcements to do the job for us. Imagine if we all did our part today, the world would be a much safer place to live in and it would be a much better place for our children’s future.
RAY MANCINI
CEO – RAY MANCINI GROUP
OPERATIONS DIRECTOR OF RAY MANCINI NATIONAL PTY LTD (SECURITY INTELLIGENCE GROUP)
INTERNATIONAL OPERATIONS DIRECTOR OF RAY MANCINI ACADEMY
FOUNDER & VICE PRESIDENT OF SAMSCATT SPORTS SHOOTING INC.
AUTHOR OF ZEN, MEDITATION & THE ART OF SHOOTING




